This is an old revision of the document!
NAS Permissions In OMV - A Primer
If preferred, this document is available in PDF form at this location → Getting Started - Permissions
General
The purpose of this document is to provide an overview explanation of access control settings, using Samba network shares, in a peer-to-peer network. It's a brief explanation of permissions, as implemented within Openmediavault's GUI, with some usable examples. It does not apply, directly, to Domains or LDAP environments.
In Openmediavault's New Users Guide, in the sections Setting up a Shared Folder and Creating a SMB/CIF “Samba” Network Share, permission selections where made that will allow all local LAN users to connect to OMV server shares with write access. For home LAN's with one or two users, this may be adequate.
On the other hand, some home users may want to prevent children from deleting files and provision to allow guest login's with Read only access. Further, small businesses may want to grant or restrict employee access to specific shares. These scenarios will require that permissions are implemented for NAS share access control.
An Immutable Law for Good Server Security
The password for the root account (the server's super user) should be strong and it should NOT be shared. While this may not be practical when operating a SOHO or business NAS server, the number of users who know the password for the root account should be held to a minimum. (In the business use case, there should be at least two administrators with root access.)
Openmediavault has another super user account “admin” that is used to log into the Web Admin GUI. Given that this user has “root user like” capabilities, admin's password should not be shared either.
The reason why it is important to control who has access to the root and admin accounts and their passwords is, this level of access can be used to override or bypass all permissions discussed in this document.
A Workstation Logon
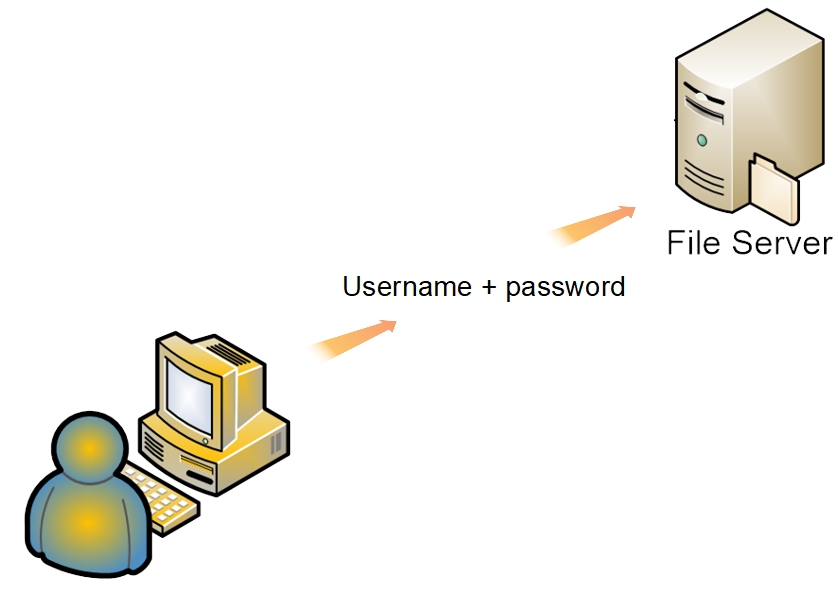
In most workgroup LAN environments, users log into their PC's using a unique username and password. These “credentials” are stored locally and have permissions associated with them that allow access to the local PC, it's folders and files, and other workstation resources. A username lookup is performed, the password is verified and if all match, access to the workstation is granted. A “local” server logon is very similar, allowing for local server administration.
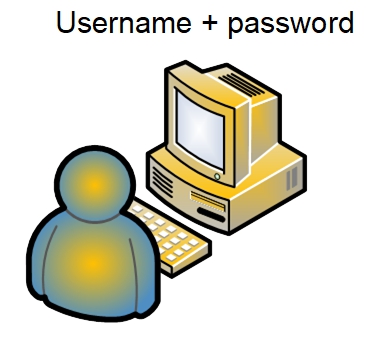
NAS Share Access
The same is true, indirectly, of network share access. When access to a network share is requested by a LAN client, there's a background authentication process taking place that is not visible to the user. When a user is logged onto a workstation, the workstation acts as an authentication “proxy”, offering the logged on user's credentials (username + password) to the server.
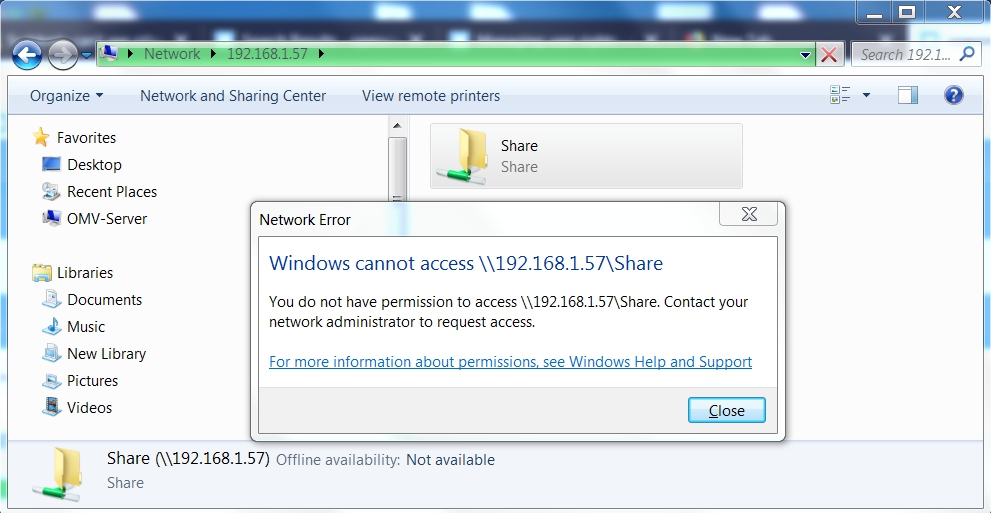
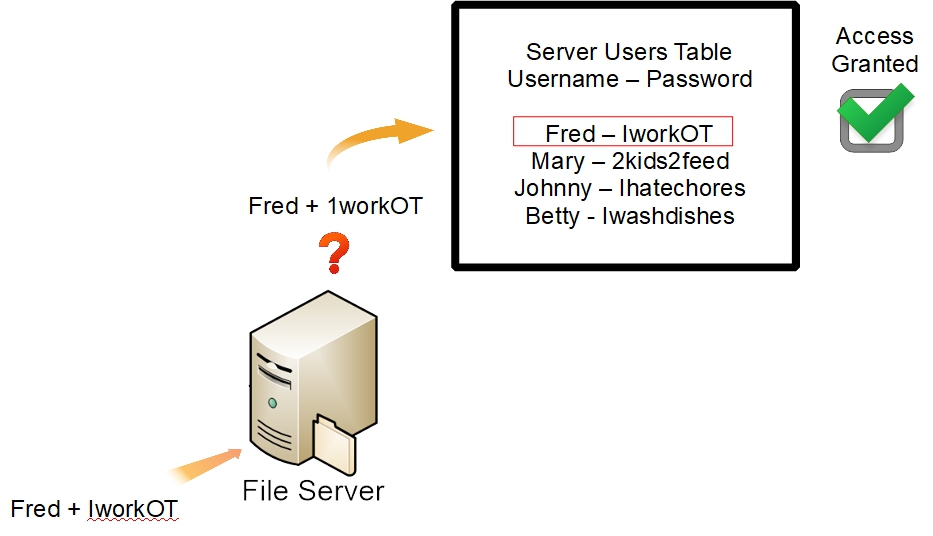
This is the basis for setting up transparent access for users, who are logged on at workstations, when they attempt to access NAS network shares.
In a workgroup environment, it's relatively easy to grant access to shares by username and password, but it requires some setup. As indicated in the above example, the Openmediavault server (hereafter referred to as OMV) needs to be aware of usernames and passwords for users who may attempt to access shares with permissions enabled.
Adding LAN Users to OMV
To enable transparent access, the first step is to add workstation usernames and their passwords to OMV.
Under, Access Rights Management, User, in the Users tab, click on the +Add button.
Name: Add the user name exactly as it is entered in the workstation logon, with capitalized letters if used.
Password: Add the username's password exactly as it is entered at the workstation.
(In this example, the eye icon was used to show the password unmasked.)
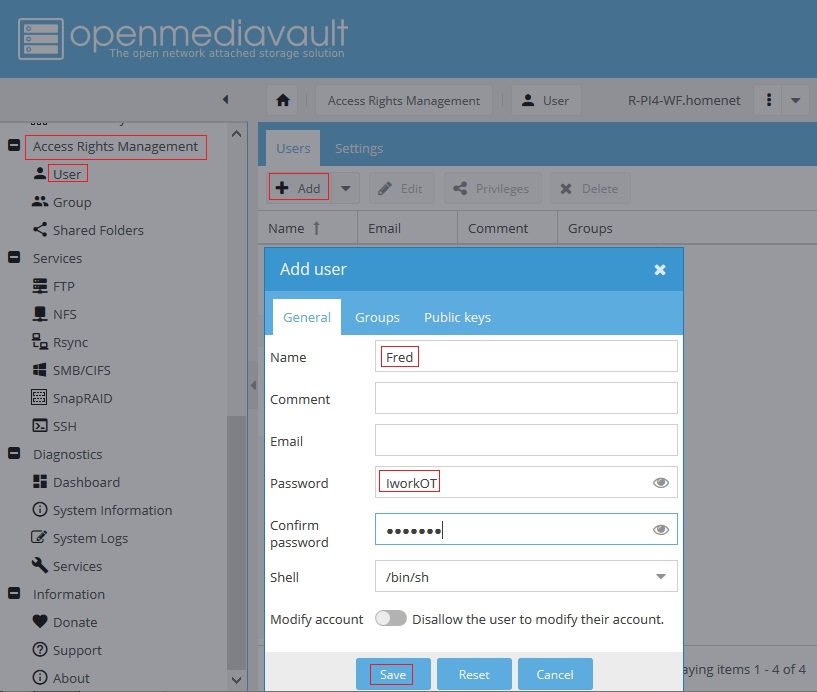
Repeat the process, adding all LAN users that will need access to the server's shares where permissions are applied.
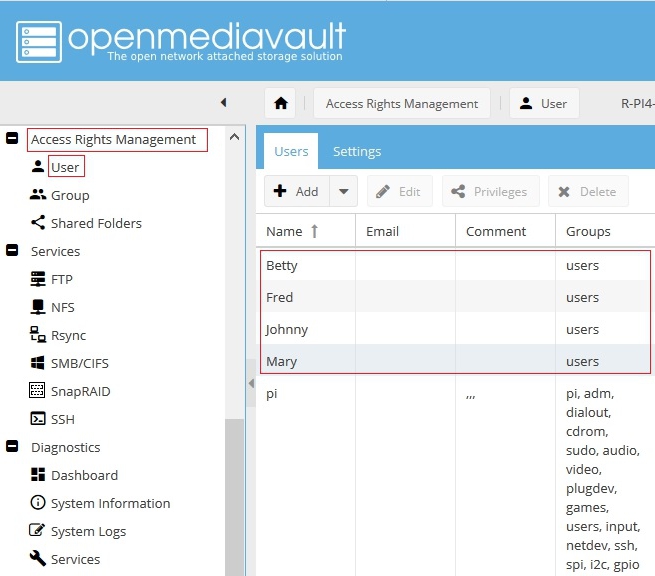
All users have been entered in OMV, by the exact username and password they use to log into their workstations, laptops, etc. Notice that all usernames are in the Group users by default.
(The pi user is a default system user installed on a Raspberry PI for administrative purposes. For the purpose of this document, the pi user can be ignored.)
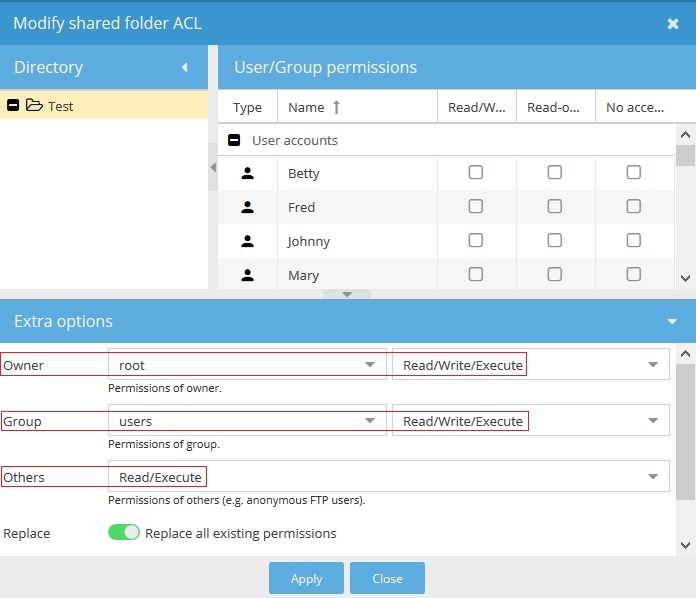
Shared Folder Permissions
By default, the majority of files and folders on the OMV file server are owned and accessed solely by the root user account. Since that is not useful in a networked environment, user access to a NAS server storage location is changed by the creation of a “Shared Folder”. Creating a shared folder is covered in the New User's Guide under Setting up a Shared Folder. This process physically creates the folder and assigns usable permissions to the folder, that allow regular user access.
The default permissions assigned to a new Shared Folder, in OMV's GUI, are:
Administrator: read/write,
Users: read/write,
Others: read-only
These permissions directly correlate to the following: